Cyber Security and Managed Services

Technology & Solutions We Use

ABOUT US
24/7 Cyber Security Operation Center


WHO WE ARE
We Spend 30,000 Hours Per Year to Virus Threats
Cyber Security doesn't have to be hard... we can do I.T. together!
The Perfect Solution For all Protection

Cyber Solutions
Ruis autem vel eum rui inea elit niau.

Network Security
Guis autem vel eum rui inea elit niau.

Web Security
Muis autem vel eum rui inea elit niau.

Locker Security
Euis autem vel eum rui inea elit niau.
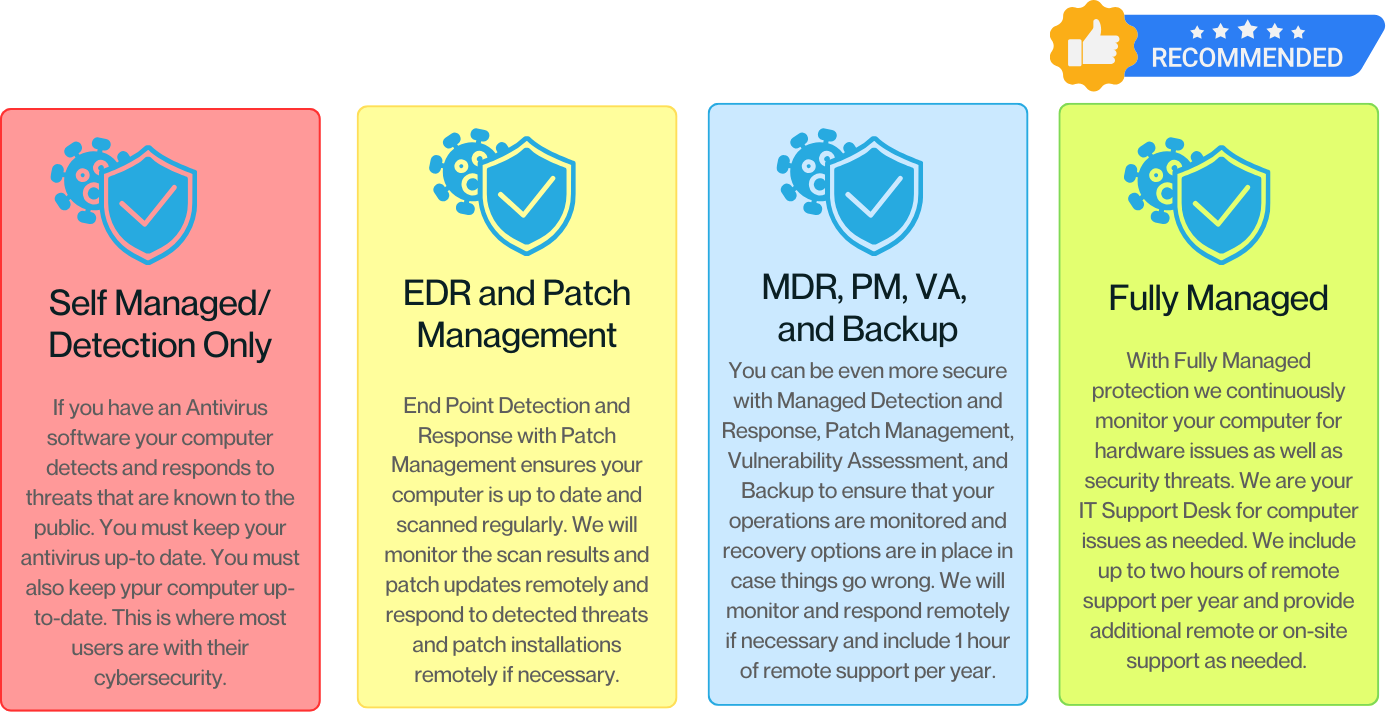
Cyber Security and
Managed Service Options
In today’s digital landscape, businesses and individuals alike face a wide range of cybersecurity threats. One of the most prevalent is **phishing**, where attackers attempt to steal sensitive information by tricking users into clicking malicious links or providing confidential data. According to a report by Verizon (2023), over 36% of data breaches in 2022 involved phishing attacks, making it one of the most common forms of cybercrime. Another major threat is **ransomware**, a type of malware that encrypts a victim’s files, with attackers demanding a ransom to restore access. The global cost of ransomware attacks exceeded $20 billion in 2021, and experts predict it could reach $265 billion by 2031 (Cybersecurity Ventures, 2022).
Other common threats include **DDoS attacks (Distributed Denial of Service)**, where attackers overwhelm a network or website with traffic to disrupt services, and **man-in-the-middle (MitM) attacks**, where hackers intercept communication between two parties to steal data or inject malicious content. Advanced **persistent threats (APTs)**, often orchestrated by nation-states or organized criminal groups, involve long-term campaigns targeting critical infrastructure or valuable intellectual property. These attacks emphasize the need for robust cybersecurity strategies, as businesses face an average of 2,244 cyberattacks daily, according to a 2022 IBM Security Report.
To mitigate these risks, implementing strong security measures like multi-factor authentication (MFA), encryption, and regular security audits is essential. As threats evolve, so must the defenses, requiring constant vigilance and a proactive approach to cybersecurity.
– Verizon (2023). *2023 Data Breach Investigations Report*.
– Cybersecurity Ventures (2022). *2022 Official Annual Cybercrime Report*.
– IBM Security (2022). *Cost of a Data Breach Report*.